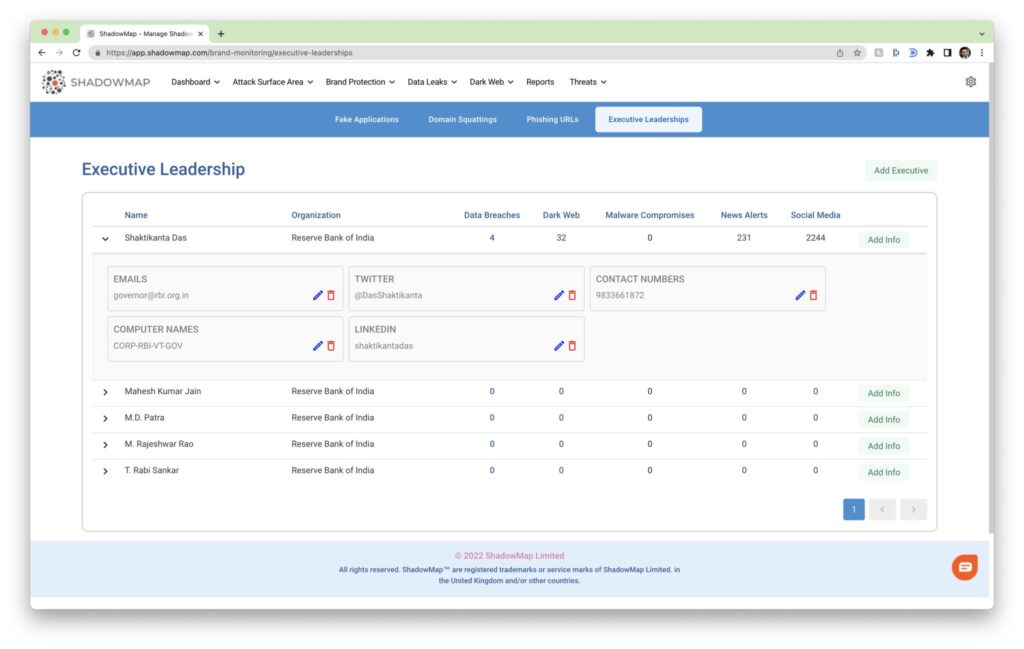
ShadowMap’s Attack Surface Management Product creates a real-time tracker of all SSO (Single Sign-On) Integrations across your organisations public footprint. A threat analysis report is generated to raise alerts for unauthorised shadow accounts and non-compliance with implementation best practices.
Key Features of ShadowMap – Tracking SSO Integrations & Threat Analysis Report
- Compatibility with: Google Workspace, Azure AD, Office 365, Okta, Cloudflare Access, Duo Security, Auth0, Amazon Cognito, Idento IAM along with internal SAML / OAuth implementations.
- Track account information behind each SSO Integration & Raise alerts for unauthorised shadow accounts.
- Automated best-practice checks of the SSO implementations to raise alerts for any privacy or security issues.
- Track Credentials Leaked on the Internet, Deep-Web & Dark-Web related to your SSO implementations.
- Have our Cyber Threat Police Experts available on-demand to investigate, analyse and mitigate these critical risks.
Importance of Ensuring Secure SSO (Single Sign-On) Implementation
A recent study on risks associated with SSO (Single Sign-On) implementations found:
- 25% of the S&P 500 and half of the top 20 most valuable public U.S companies have had at least one SSO credential for sale on the dark web in 2022.
- Shared credentials were the most common attack vector used by hackers and responsible for nearly 50% of all cyber attacks.
- Logon credentials are a major focus for external attackers (61% of data breaches involve credential data).
- With the average enterprise using over 250 cloud apps, the prospect of employees remembering unique, strong passwords for each of them is simply impractical.
- Brute force attacks accounted for 31% of all cyberattacks in 2021 and 89% of the organisations interviewed experienced phishing attacks over the past year.
Common Security Vulnerabilities in SSO (Single Sign-On) Implementations
- XML injection Attacks
- Timing or Expiration Based Attacks
- Signature Spoofing and Exclusion Attacks
- XXE and XSLT Attacks
- SSO Implementation Bypass / Authentication Bypass Attacks
- Access Token Misuse or Replay Attacks
- Credential Leakage via Referrer Header
- Client Secret Leakage
- Credential Leakage via Page Content