Phishing Takedown
Our intelligent takedown service helps you identify and mitigate the risk from Phishing URLs, Domain Squatting, Fake Websites, Fake Social Media Page & Fake Applications. By leveraging a combination of our automated workflows and expert Takedown Analysts, we can deliver industry leading response times.
In-addition to scanning the internet and helping you with continuous brand protection, our intelligent takedown service can help you takedown any offending pages, websites or applications. Our platform intelligently initiates takedown for the Phishing URLs, Domain Squatting, Fake Websites, Fake Social Media Page & Fake Applications.
- Automate Security Operations & Takedown Workflows
- Multi Pronged Approach for Rapid Takedowns – Targeting Registrars, Hosting, DNS, SSL & CDNs
- Phishing Takedown
- Website Takedown
- Domain Takedown
- Social Media Takedown
- Fake Application Takedown
- Expert Takedown Analysts
Our AI driven multi-pronged approach, along with the ability to automate security operations provides your team with the tools and ability to rapidly defend phishing attacks or fake websites, fake applications or fake social media pages that are targeting your brands.
See it in Action
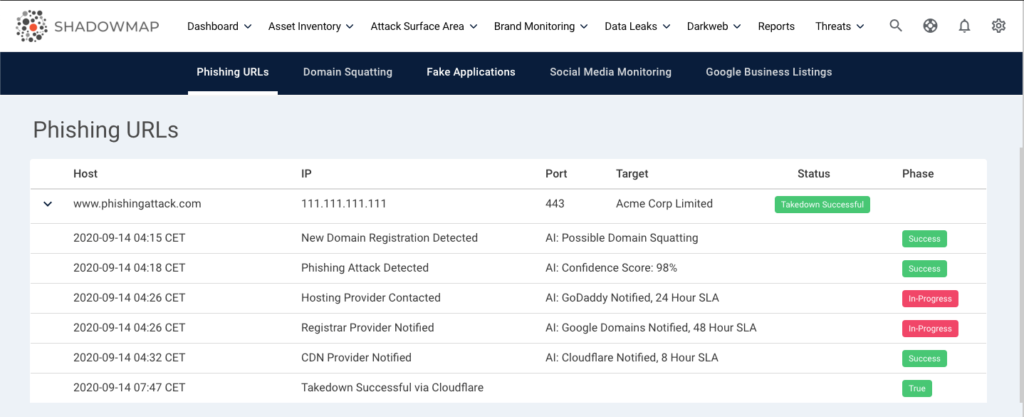
Multi Pronged Approach for Rapid Phishing Takedowns
Our Intelligent Takedown engine evaluates all the entities involved in each potential phishing attack to identify the fastest possible path to takedown the phishing pages. This includes targeting the Domain Registrars, Hosting Providers, DNS Providers, SSL Authorities, CDNs, SaaS Services, etc.
In-case of non-compliance from the initial providers contacted, the engine continues to escalate to upstream bandwidth providers, local law enforcement agencies, etc.
Automate Security Operations & Takedown Workflows
By leveraging our workflow & integration capabilities, your team can to notify various stake holders and partners of any phishing or other attacks targeting your brands. Our integrations can allow you to immediately black-list offending content across your corporate firewalls or content filters, notify relevant stake holders or drive SLAs based on response times.