ShadowMap’s AI & ML based digital risk management platform has picked up on new threat intelligence showing that hackers have released the details from 1800 vulnerable pulse VPN servers onto various deep & dark web forums. The list of 1800 servers contain several Indian entities including the Multi Commodity Exchange (MCX India), ICRA & Panasonic owned Anchor Electricals.
About the CVE-2019-11510 Pulse VPN Server Vulnerability
The critical vulnerability (CVE-2019-11510) in Pulse Secure Pulse Connect Secure, allows an unauthenticated remote attacker to arbitrary read files stored on the PCS device. The vulnerability affects versions 8.2 before 8.2R12.1, 8.3 before 8.3R7.1, and 9.0 before 9.0R3.4 of the platform.
ShadowMap’s Cyber Threat Intelligence modules have checks integrated for this vulnerability since May 2019 and will have corresponding alerts for any vulnerable servers.
Timeline
- April 24, 2019 – Pulse Secure releases initial advisory and software updates addressing multiple vulnerabilities.
- May 28, 2019 – Large commercial vendors get reports of vulnerable VPN through HackerOne.
- July 31, 2019 – Full use of exploit demonstrated using the admin session hash to get complete shell.
- August 8, 2019 – Meh Chang and Orange Tsai demonstrate the VPN issues across multiple vendors (Pulse Secure) with detailed attack on active VPN exploitation.
- August 24, 2019 – Bad Packets identifies over 14,500 vulnerable VPN servers globally still unpatched and in need of an upgrade.
- October 7, 2019 – The National Security Agency (NSA) produces a Cybersecurity Advisory on Pulse Secure and other VPN products being targeted actively by advanced persistent threat actors.
- October 16, 2019 – The CERT Coordination Center (CERT/CC) releases Vulnerability Note VU#927237: Pulse Secure VPN contains multiple vulnerabilities.
- January 2020 – Media reports cybercriminals now targeting unpatched Pulse Secure VPN servers to install REvil (Sodinokibi) ransomware.
Monitoring The Dark Web & Discovering The Breach
The initial disclosure of the breach was made by Pulse Secure through an advisory in April 2019. This vulnerability was found to be mass exploited over the last 8-9 months with a large number of vulnerable servers found to be publicly open. As part of our continuous monitoring of 4000+ Surface, Deep & Dark Web Forums, around the 4th of August, we picked up posts on various Deep & Dark Web forums where attackers had published a dump of 1800 vulnerable servers along with several sensitive details.
Inside The 1800 Vulnerable Pulse VPN Servers
On analysing the data set, we found that the leak includes the following details for each of the 1800 IP addresses listed:
- IP addresses of Pulse Secure VPN servers
- Pulse Secure VPN server firmware version
- SSH keys for each server
- A list of all local users and their password hashes
- Admin account details
- Last VPN logins (including usernames and cleartext passwords)
- VPN session cookies
On further analysis, we found several Indian entities that were a part of this breach.
Multi Commodity Exchange (MCX India)
The compromised VPN server was running the vulnerable firmware version 8.3.3.59199 included 8 internal users and 6 active sessions at the time of the breach.
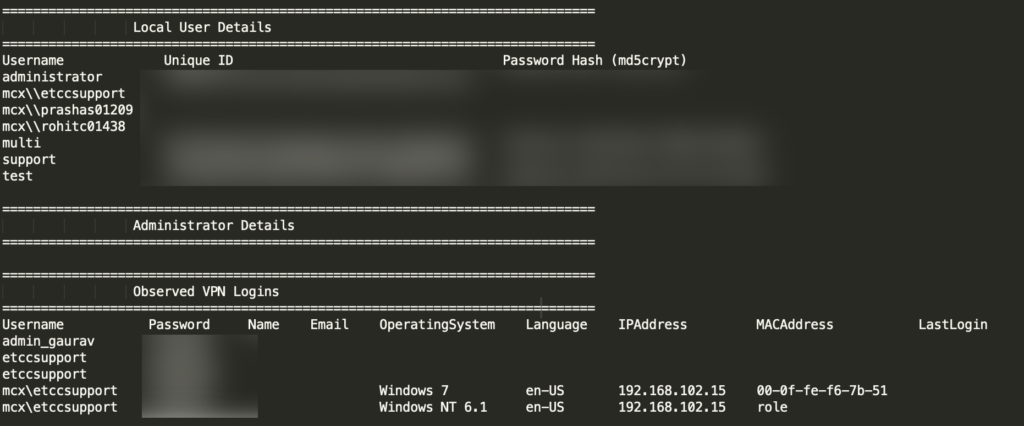
MCX India Data Leak Vulnerable Pulse VPN Servers
ICRA
The compromised VPN server was running the vulnerable firmware version 9.0.3.64015 and included 4 internal users and 6 active sessions at the time of the breach.

ICRA Data Leak Vulnerable Pulse VPN Servers
Panasonic owned Anchor Electricals
The compromised VPN server was running the vulnerable firmware version 8.3.7.65013 and included 665 internal users and 374 active sessions including both internal users and several third party consultants as well.

Anchor Panasonic Data Leak Vulnerable Pulse VPN Servers
General Recommendations
- Apply the patch as recommended by Pulse Secure.
- Review your patch management process to identify & address gaps
- Implement a hardware token, OTP or certificate based authentication to add a second factor check
- If you are a ShadowMap customer, review your Threat Intelligence alerts to identify all currently open vulnerabilities that need to be mitigated.

