ShadowMap’s AI & ML based digital risk management platform has discovered a new data breach on the darkweb that impacts 29 million users of the online dating website, Zoosk. Zoosk is an online dating service available in 25 languages and in more than 80 countries and is part of the Spark Networks SE which includes SilverSingles, EliteSingles, Jdate, Christian Mingle, eDarling, JSwipe, AdventistSingles, LDSSingles, and Attractive World.
Monitoring The Dark Web & Discovering The Breach
As part of our continuous monitoring of 4000+ Surface, Deep & Dark Web Forums for data breaches, we discovered this data being traded early last week, while it has been openly published for public consumption on the 5th of August 2020.
The data contains 29,186,600 rows of user data and the hacker has suggested that the initial breach took place in January 2020.
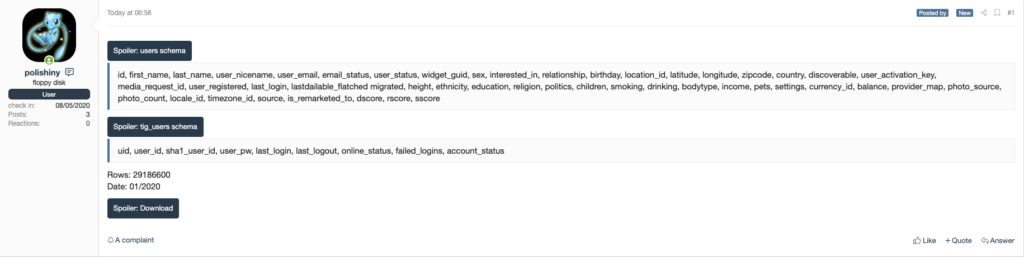
Zoosk Data Breach Published on Dark Web Forums
Inside The Zoosk Data Breach
The data contains two tables:
User Table
id, first_name, last_name, user_nicename, user_email, email_status, user_status, widget_guid, sex, interested_in, relationship, birthday, location_id, latitude, longitude, zipcode, country, discoverable, user_activation_key, media_request_id, user_registered, last_login, lastdailable_flatched migrated, height, ethnicity, education, religion, politics, children, smoking, drinking, bodytype, income, pets, settings, currency_id, balance, provider_map, photo_source, photo_count, locale_id, timezone_id, source, is_remarketed_to, dscore, rscore, sscore
Tig Users Table
uid, user_id, sha1_user_id, user_pw, last_login, last_logout, online_status, failed_logins, account_status
General Recommendations
Even though passwords were not leaked, threat actors can use the email addresses to send spam, phishing emails, and launch other online scams.
So, as a rule of thumb:
- Use strong passwords.
- Enable multi-factor authentication for all your online accounts.
- Don’t open unsolicited email attachments and links, especially from senders you don’t recognise.
- Don’t share OTPs with third-parties.
- Review online accounts and financial statements periodically.
- Regularly update your apps and any other software you use.

